Cyberspace in a Geographical Framework
Date: May 17, 1995
![]()
This paper will explore the meanings of cyberspace in depth, especially from the perspective of geography. I will relate cyberspace to the traditional core concepts in geography such as location, route, region and the users' behaviors: in what ways ar e they similar or different? Finally a humanistic approach will be adopted to examine the three levels of environment in cyberspace.
![]()
Where is your home? Where is Buffalo? The location is one of the most important concepts in geography. There are two ways to represent the location of an object. First, we can use coordinate system to record the location of some phenomena or objects in o ur real world. The location implies the geometrical meanings. Plane coordinate system(X, Y) is the easiest and most popular system. Polar coordinate system is used to calculate the point of fall of cannon balls or the orbit of planets. Cartographers use some specific coordinate systems and projection methods to represent the world on maps. Different coordinate systems could lead to different meanings of the world. There is another way to describe the location of an object. That is the "mailing address" o r we can call it "relative location". Different from the coordinate system, mailing address system shows the meaning of relationships between each area or region instead of the geometrical relationship. As at the address "100 Main Street, Buffalo, New Yor k", we can see the relationship between New York State, Buffalo, and Main Street. Our mails will be sent to their address by their address instead of the values of their coordinates.
Cyberspace also has its specific coordinate system. As I mentioned in the last paper " The New Concepts of Geographic Space: Cyberspace", the cyberspace uses IP (Internet Protocol) address and DNS (Domain name systems) to locate the tremendous compu ter sites. Both methods use tree structure to distinguish each different location and subject of machines. An IP address has four levels to consist a complete address name such as 128.130.170.14. Each level can use 0 to 255 value ( 1 byte). So, the total maximum machines used in Internet can be 4,294,967,296 units, which at present time is still adequate to accommodate a great number of sites. The IP address implies the topology and the connection of networks. Local networks usually define a "mask" to fi lter some unnecessary signals from outside networks by using "bridge" or "router"( some devices used in networks). DNS is similar to the "mailing address" in our real world. It also has tree structure and is more flexible and memorable than the IP addres s. DNS can imply the hierarchy relationship in the local network. The level of hierarchy is unlimited. The total number of a Domain Name Address could be 256 characters. It has been the most popular address systems in cyberspace. Email system or WWW uses domain name as their "mailing address" in networks.
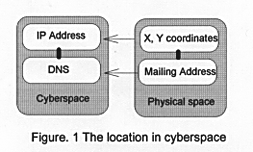
The difference between the real world and cyberspace is that the coordinate system in cyberspace does not reflect the quantitative relationship between each other. For example, we can calculate the distance between two points by their coordinates, but we can not calculate the network length between two IP addresses. What we can measure is the transmission speed and the intermediate sites between two IP addresses. The transmission speed and the intermediate sites are the major factor of influence on tr ansmitting information. I will discuss this issue later in this paper.
![]()
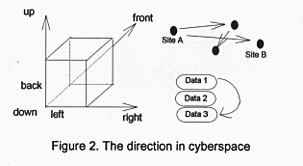
The first direction in our physical environment is up and down because of the gravity of the earth. Front and back, and Right and left are the extension of this concept. The more accurate meaning of direction is the vector from which an observer moves fr om one location to another. Although there is no gravity of the earth in cyberspace, people still need the meaning of direction to go around in networks. There are two ways to describe the meaning of direction in cyberspace. The first one is to describe t he direction from one address to another address. The second one is to simulate the physical space concepts-- Up and Down, right and left, front and back by using the technology of Virtual Reality (VR), the representation of physical objects by computer g raphics on screens. People can move the viewpoint to see different information and aspects in cyberspace. Actually, the process of the movement in VR display is identical with the first method. The only difference is the VR uses graphics to show the move ment instead of traditional text display (like telnet or gopher). The direction will have two levels. The first level is the direction from one site to another site. This movement needs physical networks as its path. The second one happens within the sam e machine or sites. The movement is from one directory or path of data to another. The second one deals with the data structure and the classification in database. The first movement is like driving a car from our home to our office building, while the second one is like walking through the different rooms of a building.
The concepts of space are also connected with the movement and direction. Thus, the route of the network and the database structure should be taken into consideration when we talk about the space meanings in cyberspace. The meanings of space are no t the same or static in different locations or machines. Some machines are more powerful and faster than others. Some machines have more advanced database systems. In addition, the space will be distorted if the topology of networks has been changed or t he data structure changed. How can the classification of information be the most efficient and accessible for users? What kind of data structure should be used in the database system? These questions are an integral part of the space meanings and the dir ection of cyberspace.
![]()
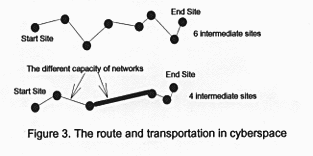
Routes are usually treated as the arcs from a start point to an end point. Usually routes have some intermediate stops like the bus routes. The function of a route is for the transportation. In cyberspace, the routes can be regarded as the connection of networks from the data sender of a machine to the data receiver of a machine. The goods of transportation are digital signals. There are protocols defined by engineers to control and manage the flow of digital signals. These digital signals are called " packages". In fact, Protocols of network decompose a whole data to different pieces as several "packages". Then these packages are sent to the next stop site in a local network. The next stop gets these packages separately and read the header of packages (their mailing addresses) and send them to the next stop site. This process will continue until the destination site receives the packages then the destination site will reconstruct the whole data and send a received signal to the original site to tell it to stop the sending of these packages. In fact, the real protocol of network is more complex and sophisticated than what I described here.
The time of transportation mainly depends on the number of intermediate sites and the capacity of the network. Some networks charge maintenance fee for the use of their networks. The use of route is almost free for users now. But in the future, some superhighways might establish a toll station in them because the use of network will be more commercial. Then we should reconsider which route will be the most economic path. Some compression technique can minimize the size of data and improve the efficie ncy of transportation. Similar to the transportation in the real world , different media of transportation ( fiber optic backbone , telephone lines and so on) have different costs and efficiency like the sea transportation and land transportation. The tec hnique of data compression also plays a very important role in data transportation.
![]()
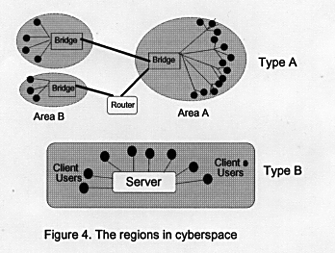
To understand the similarities and differences and to explain the interaction, communication and relationships between areas in the earth is the main purpose of geography. Geographers define region as "an area of any size throughout which accordant areal relationship between phenomena exists." The region of cyberspace could be regarded as some local networks and sites which have a similar purpose or application for users. For instance, the local network in a department or a university can be seen as one region in cyberspace. How do we define a region in cyberspace? The first step of regional study is to build a list of criteria for defining regions. The criteria and its classification should be meaningful and significant to the research topic or problems . What is the criteria of region in cyberspace? The type of machine, operating systems, TCP/IP and the topology of network can be compared to the physical criteria like the soil type, plant forms, and slopes in physical geography. The type of information server( News group, BBS, and WWW), the meaning of data, and the people can be regarded as the criteria of human geography. A core in a region is the most representative and homogenous area of regions. In cyberspace it can be the server machine or the ser ver program. Usually , bridges, routers and gateways will be regarded as the boundary of local network because these device will isolate some internal signals from outside signals to improve the efficiency of networks. Another important characteristic i n regional concepts is the regional consciousness. The people who live in the same region should have the regional consciousness. The users use the same server or network will also have the regional consciousness. The feature is very obvious in some News groups or some local IRCs. The servers or machines in a region or a local network usually have the same or similar purpose or function. The users in the same region usually have the same or similar activities, too.
![]()
The user's behaviors in cyberspace are diversified, similar to the people's behaviors in the real world, which are based on their experiences, knowledge and personal characteristics. Different type of users will have different behaviors and experience in cyberspace. The purpose and function of networks are various such as telecommunication, entertainment, education, or the search of information and so on. We can analyze the users' behaviors from three perspectives-- sociological , political and economic al. From sociological perspective, people enter cyberspace in order to expand the scope of their life. Some people try to make friends or seek love. Some want to express their bold personal opinions which they would not express to their friends in their r eal life. Cyberspace has the complementary function in social activities for each individual. From the political perspective, cyberspace provides an alternative channel to present different political opinions and improve the democracy because the governm ent can not control the communication among everybody anymore. The power od control has been decentrialized in cyberspace. From the economic perspective, the increasing commercial activities in cyberspace will lead to a revolutionary change in traditiona l trade behaviors. People can post an advertisement of their products through network. The commercial behavior becomes more flexible and personal, and is often on an one-to-one basis. In short, the users' behaviors and consumption patterns have been chan ged since the birth of cyberspace. These changes and adjustments will also have significant influences on the real world.
![]()
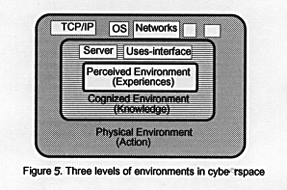
Traditional humanistic approaches in geography describe our environment as three levels: real environment, cognized environment and perceived environment. " The immanent sensation of the environment or perceived environment is the same for everyone who is exposed to the sensation , but each person will have a different "after-image" or cognized environment based on his or her own experience, knowledge, memory, etc. Our individually cognized environment constitutes the total of our knowledge of the envir onment together with our imagination of it and thought about it. These forms the foundations of our actions, which, in turn, transform the real environment" (Arild Holt-Jensen, 1988). The similar situation can be applied to cyberspace.
The users usually do not notice or perceive the physical environment in cyberspace such as the type of machines, operating systems, the protocol of networks and the topology of network. This level of environment is concerned only by the designer of netw orks and engineers. In fact, every action and movement of the users depend on the hardware and software of computers and networks. There are still many interactions between the users and the physical environment. For example, if the efficiency of the netw ork is too slow, users will complain to the system manager and the administrator of networks. Old machines will then be replaced by new workstations or a new repeater or hub will be added to their local networks to improve the speed of transmission. Eve ntually, users still transform their physical environments in order to fit their need although they may not notice the influence of their behaviors, which is like those of people transforming the real environment by their actions in real world.
What most cyberspace users know about cyberspace is their cognized environment. For example, users may not know the meanings of "package" or the function of every level of network protocols. People are only concerned with where they can get the data or use some server systems. The cognized environment contain the type of servers such as gophers, IRC, WWW, BBS, or MUD. The function and user-interface of the cognized environment will be modified and improved by the experiences of users. The improvement o f these server systems are based on the knowledge of human interface and computer technology. People will use more and more powerful and multi-function servers in the future because the knowledge is accumulating. Many kinds of servers are applied in cyber space. People use many different user-interface in cyberspace such as menu-driven, GUI (Graphical User Interface) or the VR (virtual reality) and try to find the best way to browse information or surf on the Internet. The cognized environment will automa tically evolve and be improved by the contribution of their users.
Compared to the cognized environment, the perceived environment can be the practical example of some server or machine. The home page of our geography department is a part of perceived environment. Your hotlist in Mosaic which contains your experience o f surfing cyberspace is also a part of your perceived environment. Perceived environment in cyberspace is the place which you really action and go around. You have your personal experiences and the immanent sensation in the perceived environment. You can enjoy some friendly IRC channels or hate some ironical Newsgroups. These places you love or hate are your perceived environment. Different people will have different perceived environment. Thus, the activities and forms of cyberspace are diversified. Tha t is life. That is Cyberspace.
![]()
Cyberspace is a new domain of geographical research. Although there are many differences between our real world and cyberspace, we still can find out the connection between them by using the geographical concepts. Cyberspace has its unique coordinate sys tem and the meanings of location. The routes in cyberspace influence the transportation of data or information. The regions in cyberspace refer to the local networks or servers which are homogenous or have similar functions and purpose. The users' behavio rs and experiences are diversified. No matter what level of environment the users are involved in--physical, cognized or perceived environment, there are still many interactive processes between people and cyberspace. Cyberspace change our life dramatica lly. At the same time, users' behavior also change the forms of cyberspace, like people change the natural environment. However, like people pollute this earth, cyberspace users can destroy some part of cyberspace or pollute the environment of cyberspac e, too. Therefore, the most important issue in cyberspace is to manage and preserve the information resources efficiently, as what the environmentalists do in real life. We need to explore the interaction relationship between users and their environment in cyberspace. Perhaps the theories and knowledge of geography can be the key to tackle the problems in cyberspace.
![]()
Benedikt, Michael edited, 1992, Cyberspace: First Steps, The MIT Press, Cambridge, Massachusetts.
Comer, Douglas E., Narten, Tomas, 1989,TCP/IP, chapter 3, UNIX networking, Hayden Books, pp. 49-91.
Couclelis, Helen, 1992, Location, Place, Region, and Space , Geography's Inner Worlds, Rutgers University Press, New Brunswick, New Jersey, pp. 215-233.
Holt Jensen, Arild, 1988, Humanistic approaches, Geography History and Concepts: A Student's Guide, Paul Chapman Publishing Ltd. , pp107-110.
Miles, Ian, 1991, Telecommunications: Abolising Space and Reinforcing Distance?, Cities of the 21th Century, edited by John Brotchie, Michael Batty, Peter Hall and Peter Newton, Halsted Press, pp. 73-93.
Ratan, Suneel, 1995, A New Divide between Haves and Have-Nots? , Time,Spring 1995.pp.25-26.
Rheingold, Howard, 1993, The Virtual Community, Harper Perennial.
Robinson, A.H. Sale, R., Morrison, J. and Muehrcke, P.C., 1984, Elements of Cartography Fifth Edition, John Wiley & Sons. Inc.
![]()
Assistant Professor, Geography Department, San Diego State University